Business Critical Edition | Azure (East US 2) | End-to-end: Azure + Snowflake + DNS + Validation
1. Purpose and Scope
This document provides a complete, step-by-step procedure to enable Snowflake PrivateLink on Microsoft Azure for a Snowflake Business Critical account. It includes all required creation steps (Resource Group, VNet, Subnets, Private Endpoint, Private DNS), Snowflake authorization steps, validation tests, common pitfalls, and secure methods to access Snowflake over PrivateLink from a laptop (via Bastion or VPN).
1.1 Target account details
| Field | Value |
|---|---|
| Account URL (public) | TVYPIHZ-YCA28219.snowflakecomputing.com |
| Account Locator | DLA03063 |
| Cloud | Azure |
| Region | East US 2 |
| Edition | Business Critical |
Authoritative Snowflake PrivateLink configuration (output of SYSTEM$GET_PRIVATELINK_CONFIG()):
{
"privatelink-account-name": "dla03063.east-us-2.privatelink",
"privatelink-pls-id": "sf-pvlinksvc-azeastus2prodshard2.ffc74fdb-c717-4c57-a041-8a8c52243329.eastus2.azure.privatelinkservice",
"snowpark-connect-privatelink-url": "*.snowpark.iadzpr.privatelink.snowflakecomputing.com",
"openflow-privatelink-url": "tvypihz-yca28219.openflow.iadzpr.privatelink.snowflakecomputing.com",
"app-service-privatelink-url": "*.iadzpr.privatelink.snowflake.app",
"regionless-snowsight-privatelink-url": "app-tvypihz-yca28219.privatelink.snowflakecomputing.com",
"external-telemetry-privatelink-url": "tvypihz-yca28219.telemetry.iadzpr.privatelink.snowflakecomputing.com",
"snowsight-privatelink-url": "app.east-us-2.privatelink.snowflakecomputing.com",
"regionless-privatelink-ocsp-url": "ocsp.tvypihz-yca28219.privatelink.snowflakecomputing.com",
"privatelink-account-url": "dla03063.east-us-2.privatelink.snowflakecomputing.com",
"spcs-registry-privatelink-url": "tvypihz-yca28219.registry.privatelink.snowflakecomputing.com",
"regionless-privatelink-account-url": "tvypihz-yca28219.privatelink.snowflakecomputing.com",
"spcs-auth-privatelink-url": "sfc-endpoint-login.iadzpr.privatelink.snowflakecomputing.com",
"privatelink_ocsp-url": "ocsp.dla03063.east-us-2.privatelink.snowflakecomputing.com"
}
1.2 High-level architecture
PrivateLink traffic flow:
- Client workload (VMs, apps) runs inside an Azure Virtual Network (VNet).
- Azure Private Endpoint provides a private IP in the VNet that connects to Snowflake’s Azure Private Link Service (PLS).
- Azure Private DNS resolves Snowflake PrivateLink hostnames (SQL, Snowsight, OCSP, etc.) to the Private Endpoint IP.
- After validation, Snowflake can optionally be locked down to PrivateLink-only inbound access.
-
Client / VM / App
|
| (Private DNS)
v
|
v
Azure Private Endpoint (NIC: 10.x.x.x)
|
v
Snowflake Service (Azure)
2. Prerequisites
2.1 Access and roles
3. Azure Implementation Steps (Create if needed)
3.1 Create a Resource Group (if you do not already have one)
- 1. Azure Portal -> Resource groups -> Create.
- 2. Select the subscription and region (use East US 2 for consistency).
- 3. Name suggestion: rg-snowflake-privatelink-prod.
- 4. Review + Create -> Create.
3.2 Create a Virtual Network (VNet) (if needed)
- 5. Azure Portal -> Virtual networks -> Create.
- 6. Basics: select the resource group and region (East US 2).
- 7. IP Addresses: define an address space (example: 10.0.0.0/16).
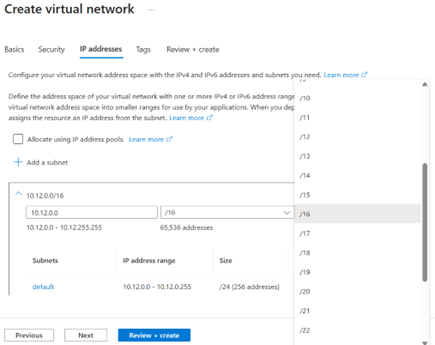
3.3 Create required subnets
3.3.1 Private Endpoint subnet (mandatory)
3.4 Create the Azure Private Endpoint to Snowflake (mandatory)
Before creating the Private Endpoint, run SYSTEM$GET_PRIVATELINK_CONFIG() in Snowflake and copy the privatelink-pls-id value.
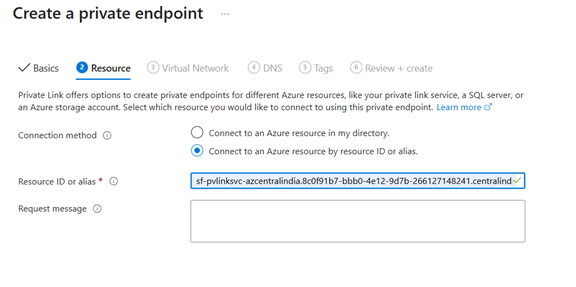
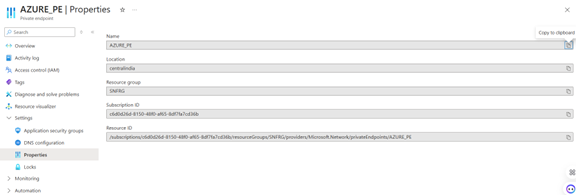
After creation, capture the Private Endpoint private IP from the associated network interface. In this implementation, the Private Endpoint IP is 10.0.0.4 (example).
3.5 Create Private DNS zone and link to VNet (mandatory)
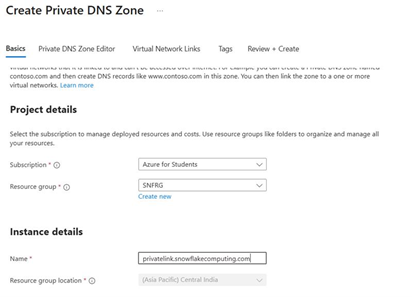
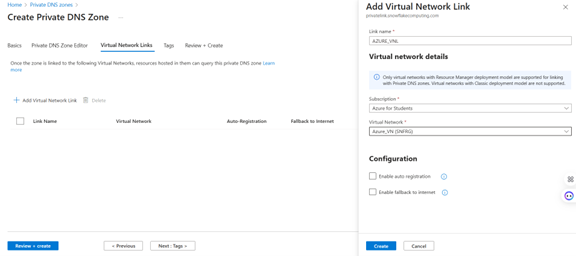
3.6 Create DNS records for Snowflake PrivateLink hostnames (mandatory)
All hostnames returned by SYSTEM$GET_PRIVATELINK_CONFIG() that end with snowflakecomputing.com must resolve to the Private Endpoint IP in your VNet. Create A records in the Private DNS zone privatelink.snowflakecomputing.com pointing to 10.0.0.4 (your Private Endpoint IP).
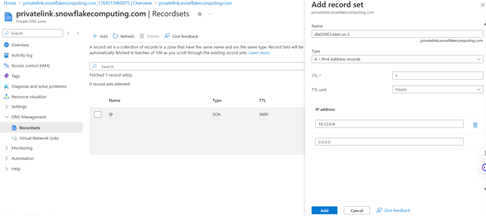
| Azure record set Name | FQDN | Purpose |
|---|---|---|
| dla03063.east-us-2.privatelink | dla03063.east-us-2.privatelink.snowflakecomputing.com | SQL endpoint (region-specific) |
| tvypihz-yca28219.privatelink | tvypihz-yca28219.privatelink.snowflakecomputing.com | SQL endpoint (regionless) |
| app.east-us-2.privatelink | app.east-us-2.privatelink.snowflakecomputing.com | Snowsight (region-specific) |
| app-tvypihz-yca28219.privatelink | app-tvypihz-yca28219.privatelink.snowflakecomputing.com | Snowsight (regionless) |
| ocsp.dla03063.east-us-2.privatelink | ocsp.dla03063.east-us-2.privatelink.snowflakecomputing.com | OCSP (region-specific) |
| ocsp.tvypihz-yca28219.privatelink | ocsp.tvypihz-yca28219.privatelink.snowflakecomputing.com | OCSP (regionless) |
| tvypihz-yca28219.openflow.iadzpr.privatelink | tvypihz-yca28219.openflow.iadzpr.privatelink.snowflakecomputing.com | Openflow service |
| tvypihz-yca28219.telemetry.iadzpr.privatelink | tvypihz-yca28219.telemetry.iadzpr.privatelink.snowflakecomputing.com | External telemetry |
| tvypihz-yca28219.registry.privatelink | tvypihz-yca28219.telemetry.iadzpr.privatelink.snowflakecomputing.com | SPCS registry |
| sfc-endpoint-login.iadzpr.privatelink | sfc-endpoint-login.iadzpr.privatelink.snowflakecomputing.com | SPCS auth endpoint |
Important DNS rules:
4. Snowflake Implementation Steps
4.1 Retrieve the PrivateLink configuration (source of truth)
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$GET_PRIVATELINK_CONFIG();
4.2 Authorize the Azure Private Endpoint in Snowflake
You need the Azure Private Endpoint resource ID and an Azure access token. From Azure CLI:
az network private-endpoint show \
--name pe-snowflake-dla03063 \
--resource-group \
--query id -o tsv
az account get-access-token --subscription
Then authorize in Snowflake (ACCOUNTADMIN):
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$GET_PRIVATELINK();
4.3 Verify authorization
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$GET_PRIVATELINK();
4.4 Optional: Enforce PrivateLink-only inbound access
Run this only after you have validated DNS + connectivity from within the VNet, otherwise you can lock yourself out.
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$ENFORCE_PRIVATELINK_ACCESS_ONLY();
Rollback if needed:
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$DISABLE_PRIVATELINK_ACCESS_ONLY();
5. Validation and Testing
5.1 Validate DNS resolution (must be done from inside the VNet)
Use a VM inside vnet-data-prod (or an equivalent workload VNet). Do not test from Azure Cloud Shell or from a laptop on the public internet.
nslookup dla03063.east-us-2.privatelink.snowflakecomputing.com
nslookup app.east-us-2.privatelink.snowflakecomputing.com
nslookup ocsp.dla03063.east-us-2.privatelink.snowflakecomputing.com
Expected result: all names resolve to the Private Endpoint private IP (example: 10.0.0.4).
5.2 Validate HTTPS and SQL connectivity
From the VNet VM:
curl -v https://dla03063.east-us-2.privatelink.snowflakecomputing.com
Snowsight (from browser inside the VNet VM):
https://app.east-us-2.privatelink.snowflakecomputing.com
5.3 Client connection strings (when connected via VNet/VPN)
Use these hostnames from SYSTEM$GET_PRIVATELINK_CONFIG():
6. Rollback steps
If you enforced PrivateLink-only access too early:
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$DISABLE_PRIVATELINK_ACCESS_ONLY();
If you need to revoke an authorized endpoint:
USE ROLE ACCOUNTADMIN;
SELECT SYSTEM$REVOKE_PRIVATELINK('');

